MultiFactor Authentication (MFA)¶
Mandatory MultiFactor Authentication (MFA) was introduced to CSD3 and storage services logins on 1st November 2022 (you can read the archived full maintenance here).
Important
- If you are a brand new internal user to the HPC service and have not submitted a HPC Account Application form, please visit https://www.hpc.cam.ac.uk/rcs-application. Do not attempt to login without submitting the form.
- If you are having trouble setting up your MFA, please consult the FAQs or watch our video tutorial
- What does this mean?
- What do I need to do?
- Walkthrough - SSH to multi.hpc.cam.ac.uk
- Walkthrough - Login-Web
- Will I need to change my working practices?
- What should I do when I change my phone?
- How do I reset my TOTP for SSH to CSD3?
- Frequently asked questions (FAQ)
What does this mean?¶
As well as your passwords and SSH keys, when you use the services, a Time-based One-Time Password (TOTP) code will be requested. This is a six digit number, refreshed every 30 seconds, which is generated typically by an app running on your mobile phone. Thus authentication will then require at least two “factors”, i.e. either password or SSH key (the first factor), plus TOTP (the second factor).
Two common such mobile apps (available from mobile app stores and tested by us) are Google Authenticator and Microsoft Authenticator, which indeed you may already have and be using for other services.
What do I need to do?¶
There are two ways to access the CSD3 services, by SSH login and login-web. You will need to set up separate authentication for each if you wish to use them. This will mean you will end up with two, different TOTP codes; the TOTP created for use with login-web appears as CSD3: your username in your authenticator app, while the TOTP created for use with SSH appears as CSD3: SSH Login in your authenticator app
I already use TOTP for other services¶
If you already use TOTP to access other services, and have a mobile application supporting TOTP to enable its use, then you will be able to SSH to multi.hpc.cam.ac.uk or login to the web site https://login-web.hpc.cam.ac.uk and feed the QR code or secret key this generates into your existing application.
Please note that we have only verified this with Google Authenticator and Microsoft Authenticator.
Follow Walkthrough - SSH to multi.hpc.cam.ac.uk. Or follow Walkthrough - Login-Web.
I do not use TOTP¶
Firstly please install the mobile authentication app of your choice (we recommend Google Authenticator or Microsoft Authenticator) onto your mobile phone, if you have no such application installed already.
Follow Walkthrough - SSH to multi.hpc.cam.ac.uk. Or follow Walkthrough - Login-Web.
Walkthrough - SSH to multi.hpc.cam.ac.uk¶
Step 0: Watch our video guide¶
If you are new to SSH and terminal use, we highly recommend that you follow the video tutorial
Step 1: Connect to special MFA node¶
When you are ready to configure TOTP, log into the special node multi.hpc.cam.ac.uk, via a terminal (not a browser). The sole function of this node is to set up TOTP if you currently have none configured.
To access the special MFA node:
ssh <username>@multi.hpc.cam.ac.uk
The first time you connect to multi.hpc.cam.ac.uk (as for any new destination with SSH) you will see a message similar to this:
The authenticity of host 'multi.hpc.cam.ac.uk (128.232.222.63)' can't be established.
ED25519 key fingerprint is SHA256:nFVSXK+VRGCaUupQEdhXzO6kp01m2fzzmbgPr0sc2so.
Please check that the fingerprint listed matches one of those listed as current at https://docs.hpc.cam.ac.uk/hpc/user-guide/hostkeys.html.
You may also see additional lines like the following:
This host key is known by the following other names/addresses:
~/.ssh/known_hosts:18: login.hpc.cam.ac.uk
(4 additional names omitted)
This is to be expected as all login nodes on CSD3 share a single set of host keys. Provided the key fingerprint is current it is ok to respond yes to the final question:
Are you sure you want to continue connecting (yes/no/[fingerprint])?
Step 2: Log into multi.hpc.cam.ac.uk¶
Once you have connected, you may see a password prompt to log in.
University of Cambridge users: You will need to enter your University password.
External users: You will need to use your SSH key or your password, depending on how your account was created.
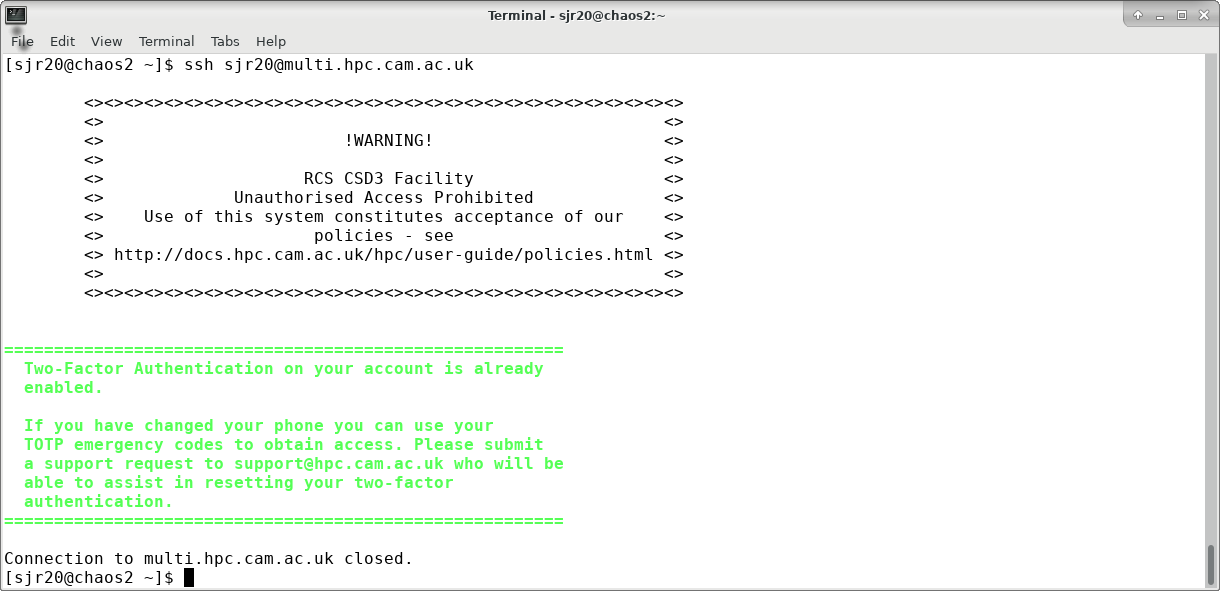
If TOTP is already configured for your account, a message will be printed and the connection closed:
Otherwise, a QR code and secret key will be printed.
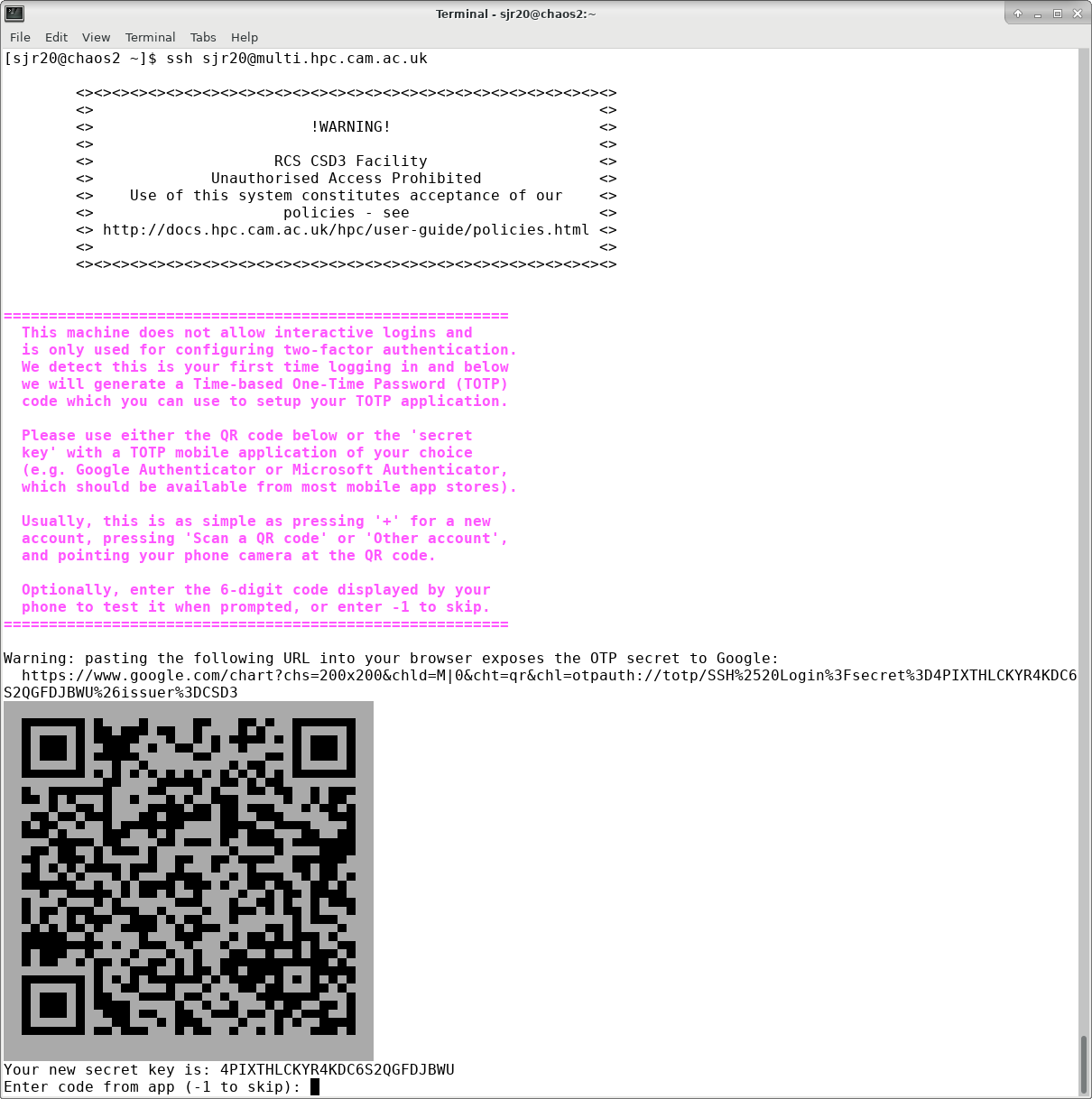
Please be careful not to point your camera at the example QR code displayed on the web page, as it will happily read it but this code is not valid for any purpose. You want to use your QR code from your login session to multi.hpc.cam.ac.uk.
Step 3: Scan the QR code or enter the secret key.¶
In your chosen authenticator app, you will want to create a new entry for your CSD3 SSH Login TOTP. In this walkthrough, we use Google Authenticator and Microsoft Authenticator as examples.
Both Google Authenticator or Microsoft Authenticator display a ‘+’ icon for adding a new account:
- Google Authenticator then presents a choice of Scan a QR code or Enter a setup key, i.e. either point your phone camera at the displayed QR code, or type in the “secret key”, respectively.
- Microsoft Authenticator presents a choice of new account type, choose Other account. This will activate the camera - point it at the displayed QR code.
Mac Users: You may find that the QR code appears distorted or broken comapred to the example found on this page. In most cases it should still scan as normal, however, you may need to enter the secret key manually as described above if the QR code does not scan.
The correct TOTP created in this way will appear in your mobile app under the account CSD3: SSH Login. Please note that a TOTP created for use with login-web appears as CSD3: your username.
Step 4: Confirm your TOTP setup¶
Once you have successfully got your CSD3 SSH Login TOTP on your chosen authenticator app, you may now check the TOTP generation works by selecting the new account and entering the 6-digit number at the prompt on your temrinal. Alternatively, skip this step by entering -1.
Step 5: Make a note of your one-time passcodes.¶
When you have confirmed your TOTP, a set of emergency one-time passcodes is then displayed. These codes will allow MFA to succeed on one occasion each if entered in place of the number generated by your app (e.g. if your phone is unavailable). Please copy these and keep them secure (the numbers displayed on the page here are of course examples only and useless):
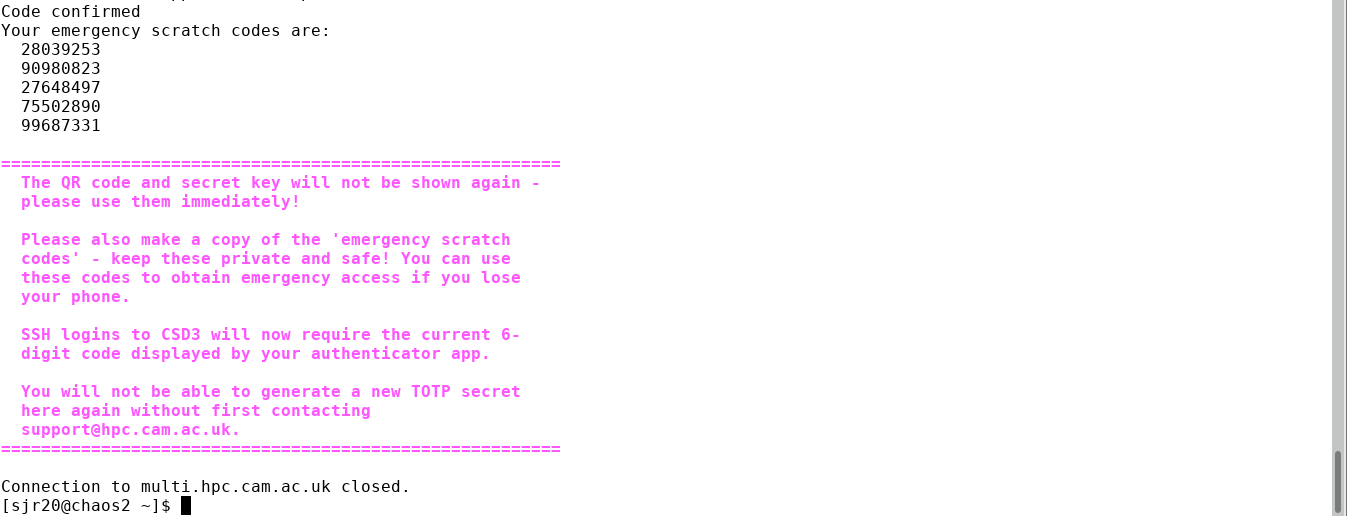
You may now safely exit your terminal and log into the cluster in the usual way. Please see our Login Guide to continue.
Walkthrough - Login-Web¶
Setting up your MFA for login-web is a simple process. Whether you are logging in for the first time or after getting your MFA reset, you will need to visit https://login-web.hpc.cam.ac.uk, enter your CSD3 credentials to login. You will then be presented with the QR code that you can scan into your authentication app. The correct TOTP created in this way will appear in your mobile app under the account CSD3: your username.
Will I need to change my working practices?¶
People work in different ways, and the answer to this is “possibly”.
Adding a second factor to authentication definitely increases the work required to login, but not having the feature on CSD3 is no longer acceptable. The support team have been using MFA themselves for some time without issue.
Reducing the effort of MFA - connection sharing¶
If you make many separate connections per day to CSD3, then you may find yourself reaching for your phone many times. However it is possible to streamline this by multiplexing SSH connections, e.g. the following section in your ~/.ssh/config file, on your local machine, would create an initial network connection (requiring MFA) to a login node, which subsequent SSH sessions (to the same login node) would reuse (so only one use of the mobile phone but possibly many sessions):
Host login*.hpc.cam.ac.uk
ControlMaster auto
ControlPath ~/.ssh/control-%C
ControlPersist 900
(see the Control* directives in the ssh_config manual page for OpenSSH).
Note that once inside the cluster, it is possible to move laterally to other nodes without additional MFA. E.g. if you have a session already on login-p-1.hpc.cam.ac.uk but would like to use login-q-1.hpc.cam.ac.uk instead, then you can
- either start again and SSH from your local machine to login-q-1.hpc.cam.ac.uk (with another round of MFA)
- or you can simply type ssh login-q-1 from inside your original login-p-1 session.
In some cases (e.g. automated connections out of office hours) another solution may be required and the support desk will be able to help.
What should I do when I change my phone?¶
If you plan to change your phone, please consider transferring your TOTP secrets to your new device while you still have access to the old one. For example, the Google Authenticator app has a Transfer accounts option under its settings menu which provides a simple way of copying the secrets to the new device. The commonly recommended Microsoft Authenticator app requires a personal Microsoft account to be attached to the app to act as a cloud backup for TOTP secrets transfer, please keep this in mind when setting up your authentication app or when changing phones.
If you are passing on the old device to another person, you should perform a wipe to factory settings first.
If you lose your old device, or pass it on without wiping it, you will need to reset your MFA tokens - please see How do I reset my TOTP for SSH to CSD3?.
How do I reset my TOTP for SSH to CSD3?¶
If you need to reset your TOTP second factor, e.g. because you no longer have access to your original phone, please contact support@hpc.cam.ac.uk. The TOTP second factor is an important protection against user account compromise, and an identity check is therefore needed when a request to replace it is received. This is similar to the existing process for resetting University passwords in a context where face to face identity checks are not feasible most of the time.
When contacting the service desk to request a reset of MFA, please be sure to send the email from the email address we have registered against your user account.
The service desk agent will arrange a time at which to hold a brief video call with you at which you will be asked to present photographic proof of identity in the form of one of the following:
- Passport
- Driving licence
- University card (for members of the University of Cambridge).
Expired forms of the above are acceptable as proof of identity. Following completion of this check, the TOTP secret will be reset and you will be able to revisit multi.hpc.cam.ac.uk to repeat the setup procedure.
Frequently asked questions (FAQ)¶
I am unable to login to multi.hpc.cam.ac.uk and now I get “Connection refused”.
- Make sure you are using the same userid, password or public key as you would to login.hpc.cam.ac.uk. As with the login nodes, failing to authenticate three times in succession to multi will cause your address to be blocked for 20 minutes, so if this happens please wait this long before trying again.
I am using MS Authenticator but the TOTP code doesn’t work.
- If you still have the QR code and secret key on your screen then delete the account in your Authenticator and recreate it, making sure that the account is of the Other type (not Personal or Work). Otherwise please contact support@hpc.cam.ac.uk to request reset of the MFA secret before trying again, and select account type Other.
When performing ssh to multi.hpc.cam.ac.uk the QR code is replaced either by garbage or is broken up by blank lines, making it unusable.
- Setting export LANG=en_GB.UTF-8 in Mac terminals before performing the ssh may stop this happening - however if this has already happened you will need to contact support@hpc.cam.ac.uk to request reset of the MFA secret before trying again.
Connection sharing doesn’t work with Filezilla and I keep seeing TOTP requests during file transfers.
- Please prefer to use the RDS gateway rds.uis.cam.ac.uk for file transfers. This will request TOTP less frequently.
I don’t have a smart phone on which I can install an OATH-compliant TOTP app such as Google Authenticator, Microsoft Authenticator, Authy or FreeOTP.
- The proper solution for you is to ask your department to purchase an inexpensive OATH TOTP compatible token device.
- If you already have such a device and use it for login to another service, you will need a new device for use with CSD3 unless it supports multiple accounts.
- Any device needs to support 6 digit, SHA1 OATH TOTP with 30 seconds time interval, which non-programmable devices may well not do. In particular, please note that the SafeID/Classic model provided by the UIS for Microsoft services is known not to work with the Google style of TOTP used on CSD3.
- YubiKeys (used in conjunction with an application on phone, desktop or laptop) are known to work (although we have not been able to test all combinations of device and platform).
- Combinations of hardware token and platform which we have tested and are known to work are listed below (please note that these are not recommendations, merely examples which we have made to work):
- YubiKey 5Ci (has USB type C plug) with Microsoft Windows laptop or Android phone.
- Nitrokey Pro 2 (has USB type A plug) with Linux desktop.
- There will be others - if you identify a new token device which demonstrably works with CSD3, please let us know and we will list it here.